check_scan.sh
an unofficial nmap scanner plugin for nagios that I wrote to satisfy my own needs.
Here's what it does:
On the initial scan, it creates a baseline scan for future comparison.
On each subsequent check, it compares the new scan against the baseline.
Changes are reported in “warning” status, showing the open port.
check_scan.sh does a “TCP connect scan”, so it doesn't have to run as root.
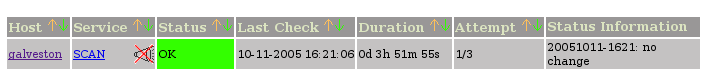
Screen shots of nagios, check_scan.sh as a service:


To use
Just copy everything between the dotted lines, then paste the text into an empty
text file that you can modify to work as a shell script. My nagios plugins are
owned by root.root and located in the /usr/lib/nagios/plugins directory, so that's
where I put it, doing a “chown root.root” then “chmod 755” like all the other plugins.
If you don't know how to use nagios, RTFM (no offense intended), but the
“quick-n-dirty” instructions are:
Once you've got the script in the plugin path (such as /usr/lib/nagios/plugins)
And, it has the proper ownership and permissions (chown root.root, chmod 755)
add to checkcommand.cfg: command[check_scan]=$USER1$/check_scan.sh -H $HOSTADDRESS$
(if you get an error with that syntax, copy the below “define command” format)
or, for Debian Sarge (like me), in /etc/nagios-plugins/config create a file (such as scan.cfg) with the
following information ( i just copied ftp.cfg and changed that):
define command{
command_name check_scan
command_line /usr/lib/nagios/plugins/check_scan.sh -H $HOSTADDRESS$
}
edit /etc/nagios/service.cfg (sample):
define service{
use generic-service
host_name galveston
service_description SCAN
is_volatile 0
check_period 24x7
max_check_attempts 3
normal_check_interval 5
retry_check_interval 1
contact_groups security
notification_interval 240
notification_period 24x7
notification_options c,r
check_command check_scan
}
Once all that is done, you should be able to do an “/etc/init.d/nagios reload”
It works for me. Your mileage may vary. :) Yes, I know the code isn't
fancy, and it's not the official plugin format, and may cause cancer in
rats. If that concerns you, fix it, don't use it, whatever.
If you find any errors, or have any suggestions, please email me at:
mark AT altsec.info
And, please please please support nagios, nmap, and the other fine
open source people out there. It's a GNU day dawning.
P.S. Did I mention that this has been tested only on Linux?
The body of check_scan.sh
(copy it, or save this link)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
#!/bin/sh # check_scan.sh
# works as a
nagios plugin to do an nmap scan of a system
# The difference
between this script and what I've seen elsewhere
# is
check_scan.sh provides a baseline of scan data for comparison.
#
#
Copyright (C) 2005 Mark Stingley
# mark AT
altsec.info
#
# If you need help with your security or systems
administration,
# see http://www.altsec.info
#
#
Dependencies: nmap, nagios, linux
#
# README: (1) check the
variables below in the section named
# SET THESE VARIABLES. Also,
verify the path for
# the GNU/Linux utilities referenced
# (2)
the other requirement is a directory that the
# nagios user can
write to. I used /etc/nagios,
# since the directories created
there contain
# baseline nmap scan data
# (3) the scan files
are kept in /etc/nagios/scancheck
# in the scans directory. The
last scan is simply
# named by the ip address of the host, such
as:
# 192.168.25.3. The baseline scan for that host
# would be
192.168.25.3.base
# (4) to modify the baseline and eliminate
warnings
# about ports, edit the scan file IP-address.base
# in
/etc/nagios/scancheck/scans. Just be sure
# that the data is a
default "sort", or comparison
# won't work. The
alternative is to simply cat
# the last scan file to the baseline,
such as:
# cat #.#.#.# > #.#.#.#.base
#
# Installation:
simply copy this script to your plugin directory,
# make sure it
is executable and has the proper
# ownership
#
# This
program is free software; you can redistribute it and/or modify
#
it under the terms of the GNU General Public License as published
by
# the Free Software Foundation; either version 2 of the
License, or
# (at your option) any later version.
#
# This
program is distributed in the hope that it will be useful,
# but
WITHOUT ANY WARRANTY; without even the implied warranty of
#
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
# GNU
General Public License for more details.
#
# See
http://www.gnu.org/licenses/licenses.html#GPL or write to the
#
Free Software Foundation, Inc., 59 Temple Place, Suite 330, Boston,
#
MA 02111-1307 USA
#
# Changelog:
# 20051011 revised from a
2004 script "scancheck.sh"
#
# ToDo:
# 1. rewrite
in perl or C
# 2. incorporate exclusion lists
# 3. incorporate
critical port lists
#
# - - - - - - - - SET THESE VARIABLES - -
- - - - - - - - - -
BASEDIR=/etc/nagios/scancheck #where to keep
everything
#must be nagios user writable
NMAPPATH=/usr/bin
#where is
nmap
#------------------------------------------------------------
#note...
to run manually, you have to supply a dummy
#argument 1, since the
ip address is arg2
IP=$2
if [ ! "$IP" ];
then
echo "No IP address supplied"
exit
0
fi
SCANDIR=$BASEDIR/scans
FILEDIR=$BASEDIR/files
CHANGED=0
INITIAL=0
if
[ ! -d $BASEDIR ]; then
mkdir $BASEDIR
fi
if
[ ! -d $SCANDIR ]; then
mkdir $SCANDIR
fi
if
[ ! -d $FILEDIR ]; then
mkdir $FILEDIR
fi
if
[ ! -f $SCANDIR/$IP.base ]; then
touch
$SCANDIR/$IP.base
INITIAL=1
fi
SCANTIME=`/bin/date
+%Y%m%d-%H%M`
/usr/bin/nmap -sT -P0 $IP | /bin/grep -w open |
\
/usr/bin/sort > $SCANDIR/$IP
DIFF=`/usr/bin/comm -23
$SCANDIR/$IP $SCANDIR/$IP.base`
if [ "$DIFF" ];
then
CHANGED=1
DIFFSTR=`echo "$DIFF"
| /usr/bin/awk '{print $1}' | \
/usr/bin/paste -s -d
" " -`
fi
if [ $INITIAL -eq 1 ]; then
/bin/cat $SCANDIR/$IP > $SCANDIR/$IP.base
echo "Initial
scan"
exit 0
fi
if [ $CHANGED -eq 1 ];
then
echo "Scan $SCANTIME: NEW $DIFFSTR"
exit 1
else
echo "$SCANTIME: no change"
exit 0
fi
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Copyright © 2005 Mark Stingley